5 ways companies violate HIPAA compliance (and how to avoid them)
HIPAA compliance can be an Achilles’ heel for the companies who fall under its regulatory umbrella. And rightfully so. After all, the protected health information (PHI) it mandates is among the most sensitive data that businesses in any industry handle.
Failure to comply can lead to large fines and legal penalties. Or even drive companies out of business altogether over time. That’s why it pays to be prepared for the threats. But preparation is a tall order when the threats come from every direction, including external intruders and the very people you trust to access it.
Here are 5 ways that companies violate HIPAA compliance, and how to avoid them.
Malware and hacking
As with any industry, malware and hackers are a real concern for HIPAA-compliant companies. But the risks are even higher when data loss results in fines and legal action, in addition to lost productivity or downtime.
The good news is, there are a number of strategies you can take to keep your network safe and meet compliance mandates. Four of the most direct methods include:
- Requiring updated passwords on a minimum quarterly basis.
- Making sure your company has adequate firewalls in place to protect your network.
- Requiring a base level of password complexity.
- Making sure software is updated at all times to shore up security vulnerabilities.
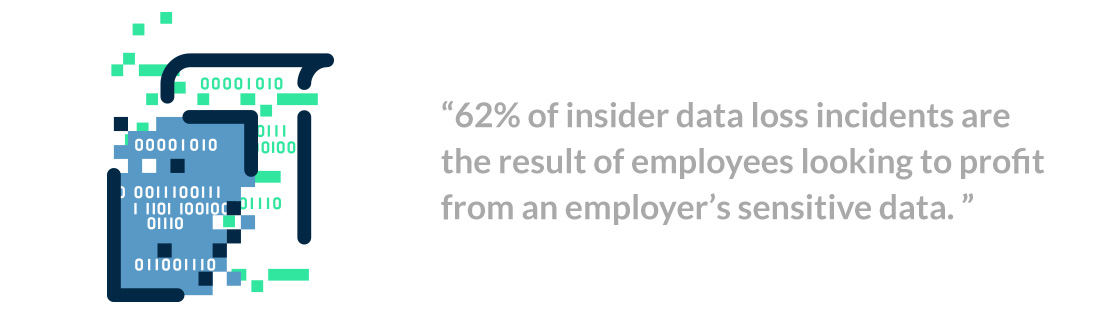
Malicious (or absent-minded) insiders
We’d all like to believe we can trust the people we work with. Unfortunately, this isn’t always the case. Often it’s the very people we allow inside our networks who do the most damage. Sometimes for profit.
However, there are a few solid strategies you can take to minimize exposure:
- Practice the principle of least privilege for employee access to PHI.
- Use keycard access points to control access to hardware portals. Never provide access to employees who do not require it.
- Track and monitor who accesses PHI, and when.
Lost or stolen devices
With the rise of cloud computing, businesses frequently use portable devices such as tablets or laptops. This doesn’t have to lead to a compliance issue should one of these devices be lost or stolen. But it can. Here are two strategies to avoid violating compliance should one of your devices be lost.
- Install and maintain remote wipe programs on any devices that can access PHI. This is particularly important if your employees will ever access PHI from public networks (consider a policy against such use). Require automatic logout / session timeouts for sensitive programs.
- Require all devices that access your network to be password-protected.
Improper device or records disposal
Does your office use devices such as copy machines? Often these devices save document copies on their hard drives. That means they may retain copies of peoples’ PHI. What do you do with outdated records, and how do you handle document transfer risks? Here are a few tips:
- Have a plan to clear temporary files from all devices that handle copies of any files or messages containing PHI.
- Always shred discarded hard copies or securely store outdated / old records that are no longer actively used.
Third-party disclosure
The nature of PHI is that this sensitive information often needs to move from office to office or organization to organization during the course of patient care. These transfer points are high-risk areas where you can violate compliance and compromise patients’ data. Try these strategies to make records transfer more secure:
- Have a plan in place for transferring records in a secure, encrypted or otherwise protected manner.
- Require a business associate agreement with any agency that will exchange information with your organization. This agreement should clearly outline responsibilities, protocols and best practices.
Conclusion
It’s clear that HIPAA compliance is a complex issue. You probably need professional planning and security to prevent data loss and the resulting fallout. It’s highly advisable that you consider reaching out to a Managed Services Provider (MSP) with HIPAA experience who can guide you through the process.
They can also provide strategies and solutions to achieve maximum protection for your unique organizational needs and risks. Given the steep fines and extreme cost of downtime or data loss, this will likely save you money in the long run.