The “WannaCrypt” Global Cyberattack
On Tuesday, May 12th, we were introduced to unprecedented global cyberattacks known as “WannaCrypt” or “WannaCry”. This prolific ransomware attacked and infected tens of thousands of Windows-based servers and workstations, critically impacting financial firms, transportation infrastructure, and even the British National Health Service.
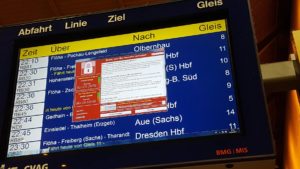
Infected German Train Departure Signs (Source:DPA)
Our clients receive regular security updates that guard against WannaCrypt and future variants.
Towards the end of last year, Microsoft started warning customers about best security practices with regards to Windows devices and the SMB protocol. The National Security Agency developed tools that could gain unauthorized access by exploiting Windows vulnerabilities, and likely used them to monitor the SWIFT interbank messaging network.
Rumors of the theft of the NSA’s hacking tools started to spread, and by February, the NSA alerted Microsoft so vulnerabilities could be addressed. In March, Microsoft quietly released security updates. By April, the hacking tools were publicly released.
On May 12th, hackers started deploying new ransomware, leveraging techniques used by the NSA hacking tools. Companies without up-to-date devices became a prime target — particularly businesses still using unsupported systems as Windows XP and Server 2003.
We anticipate variants of this attack to continue over the next few months. Unsupported and non-updated Windows systems will remain at risk.
![]() Guidance for the Home
Guidance for the Home
- Update Windows
- Verify Backups
- Install Antimalware Software

